How to Prevent Online Frauds in Your Web or Mobile Application: A Complete Guide
Online fraud has become one of the biggest threats to digital businesses today. Whether you’re running a full-scale e-commerce platform, a mobile wallet app, or a SaaS product, fraudsters…
Read MoreSecure Authentication Explained: How to Keep User Accounts Safe from Hackers
In today’s digital-first world, user accounts are under constant threat. From brute-force attacks to phishing scams, hackers are more creative—and persistent—than ever. That’s…
Read MoreWhy Network Security Is Critical for Your Online Business
In today’s digitally driven world, online businesses are booming—and so are cyber threats. Whether you’re running an e-commerce store, a SaaS platform, or a digital service,…
Read MorePhishing Detection in Cybersecurity: Staying Ahead of Digital Deception
In today’s digital-first world, cybersecurity threats are growing in both volume and sophistication. Among the most deceptive and widespread threats is phishing—a type of cyberattack…
Read MoreUnderstanding Behavioral Analytics in Cybersecurity
In today’s digital world, cyber threats are becoming more complex, unpredictable, and stealthy. Traditional security measures like firewalls and antivirus software, though …
Read MoreData Privacy & Marketing Compliance: Navigating GDPR, Cookie-less Tracking, and Ethical Advertising
In the digital age, where consumer data fuels marketing strategies, data privacy and compliance have become more critical than ever. With increasing regulations like the General…
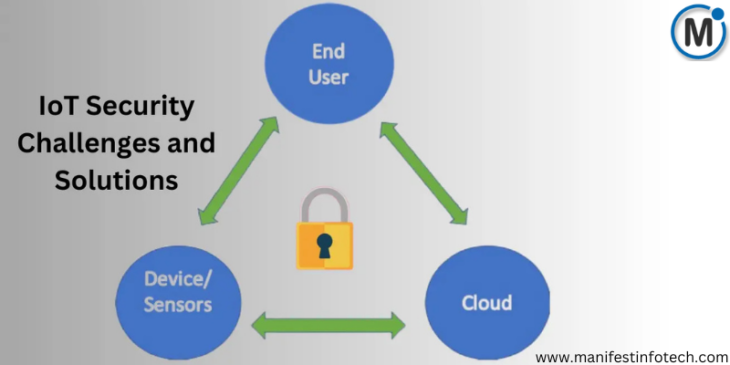
Read MoreIoT Security Challenges
The Internet of Things (IoT) has revolutionized the way we interact with technology, connecting billions of devices worldwide. From smart homes and wearable gadgets to industrial…
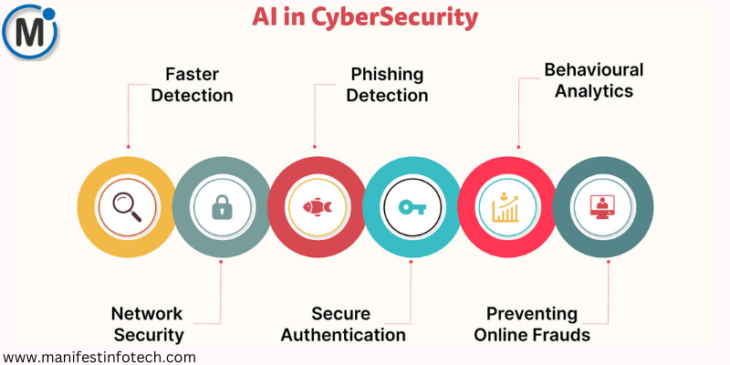
Read MoreThe Role of AI in Enhancing Cybersecurity
In today’s digital world, cybersecurity threats are evolving rapidly, making it increasingly challenging for organizations to protect sensitive data. Artificial Intelligence…
Read MoreData Privacy Regulations and Best Practices: Safeguarding Sensitive Information
In an era where data is the new currency, protecting personal and sensitive information has become a critical concern for individuals, businesses, and governments alike. Data privacy…
Read MoreThe Latest Cybersecurity Threats and How to Prevent Them
With the rapid advancement of technology, cybersecurity threats are becoming more sophisticated and prevalent. Businesses, governments, and individuals are all at risk of cyberattacks…
Read More